I have started a discussion about openscap HTML report redesign.
Gathered feedback
This was gathered from comments on the referenced blog post, the openscap, scap-workbench and scap-security-guide mailing lists.
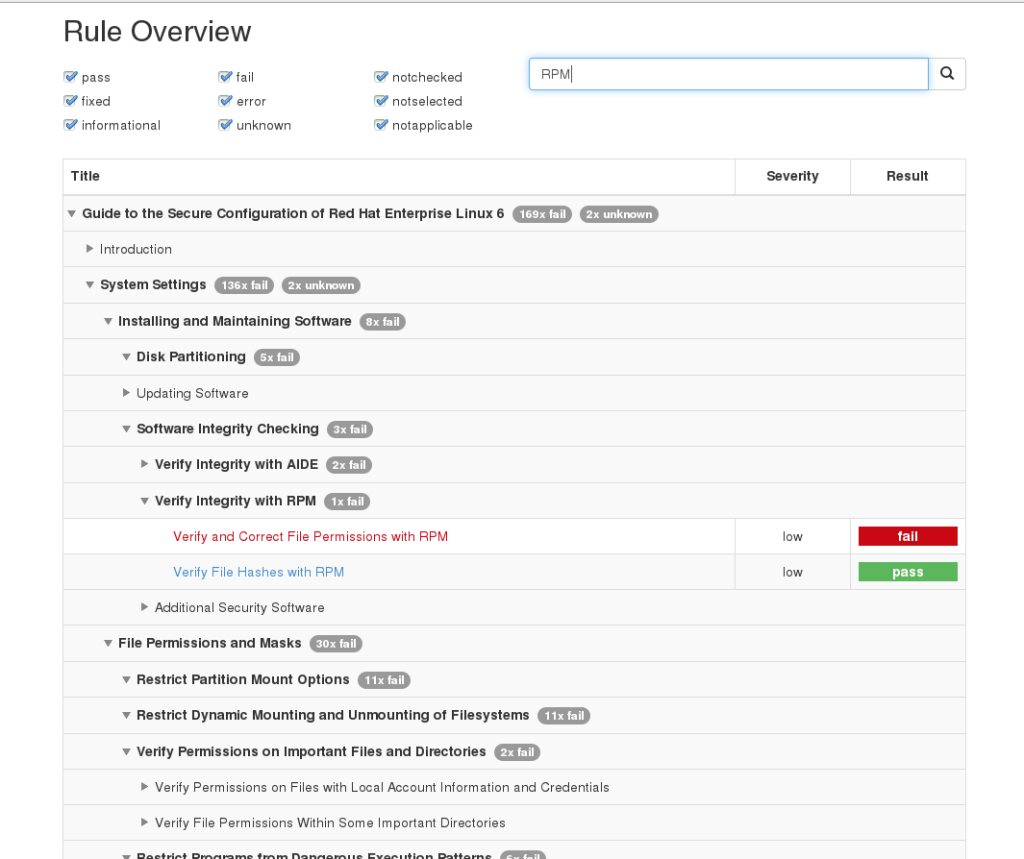
- search through XCCDF rules (identifiers, title, ID, description, …) – implemented
- filter by XCCDF result – implemented
- use HTML anchors, speed up navigation between result details and result overview (jquery popup?) – implemented
- too many colors in the introduction section – hopefully fixed
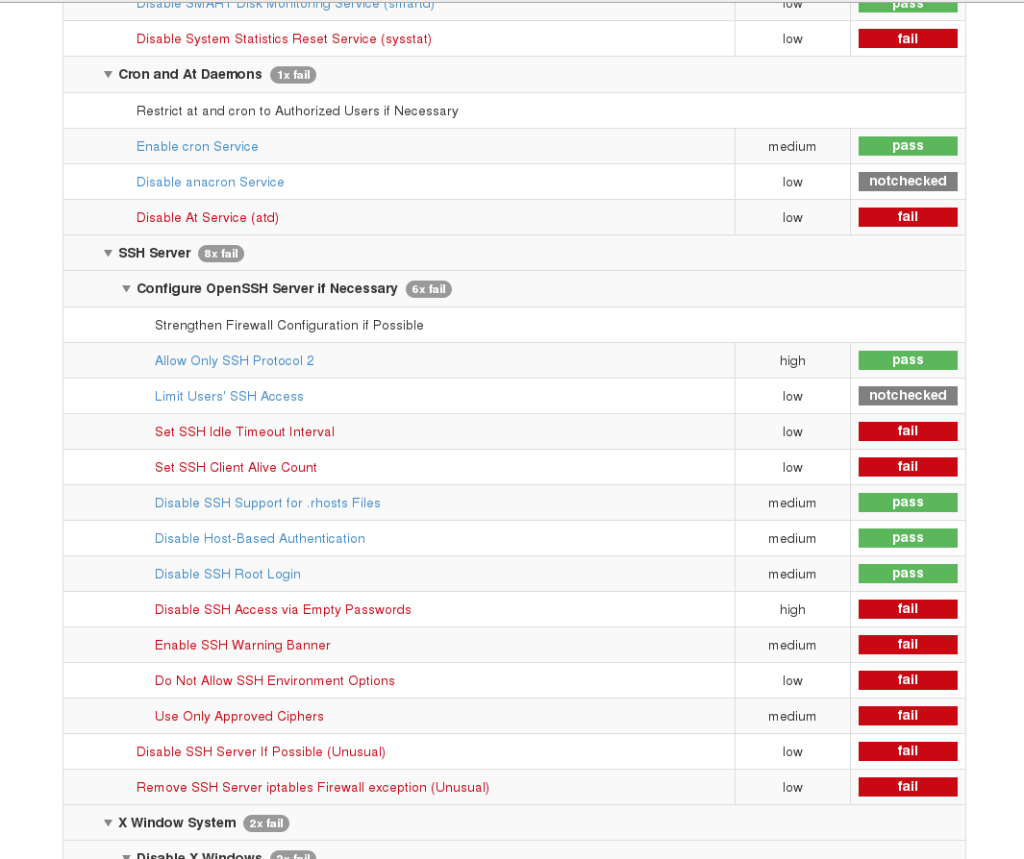
- organize rule results into groups, display rule overview as a tree – implemented
- show severity in rule overview – implemented
- report fail and error rules by severity in addition to the standard XCCDF score system – TODO
- sort by severity in rule overview – TODO
- sort by identifiers in rule overview – TODO
- false positive waiving, other means to pass feedback about why rule fails – probably out of scope, would need a new file format to store the waivers
xslt-devel branch
I have created a new branch in the openscap repository where I am continuing with this effort. Instead of a prototype HTML the repo has working XSLTs. Keep in mind that the branch breaks openscap tests and you can’t generate HTML report using the oscap tool command line. Instead you have to use xsltproc directly for now.
https://git.fedorahosted.org/cgit/openscap.git/log/?h=xslt-devel
Screenshots
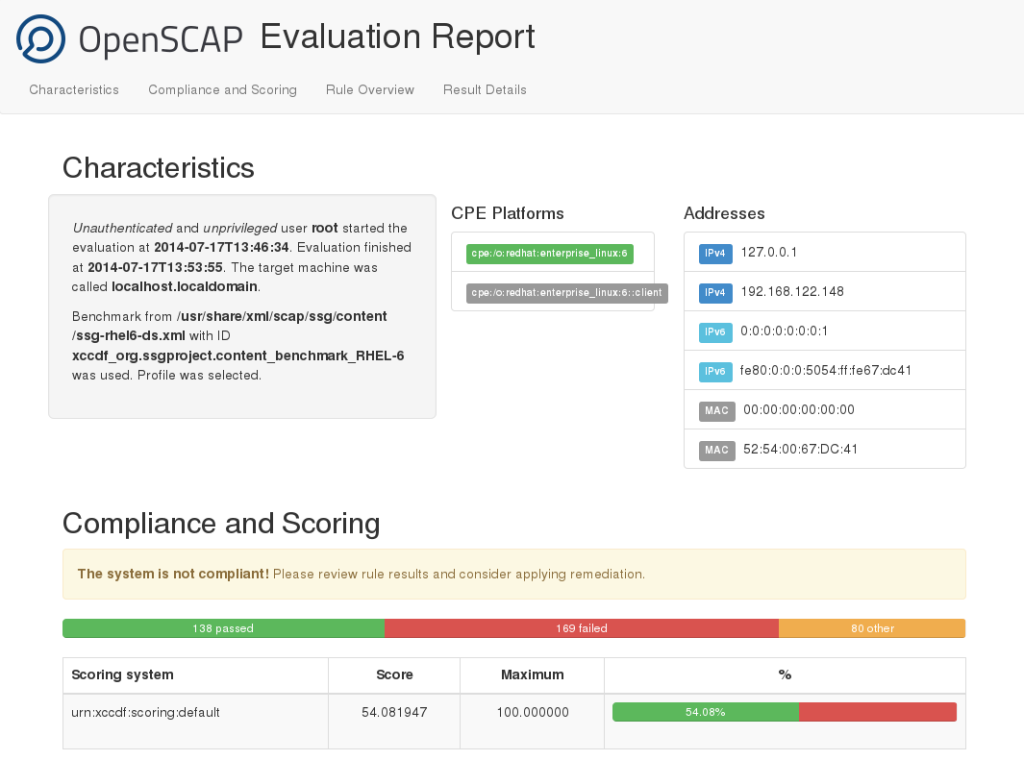
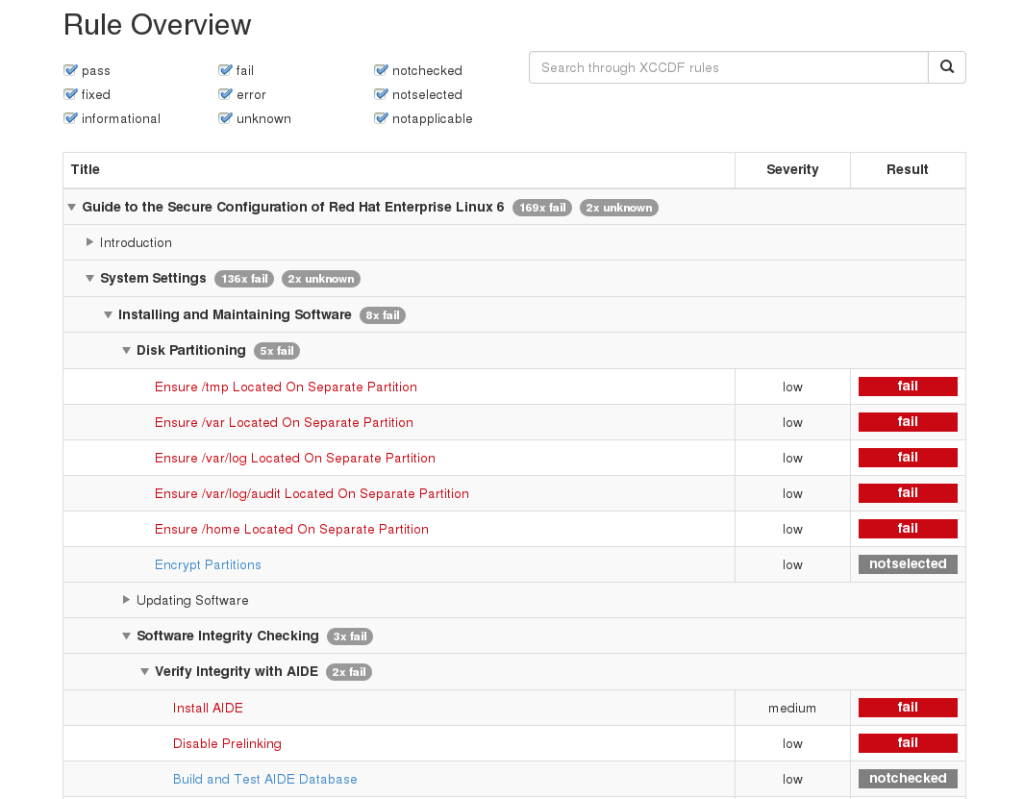
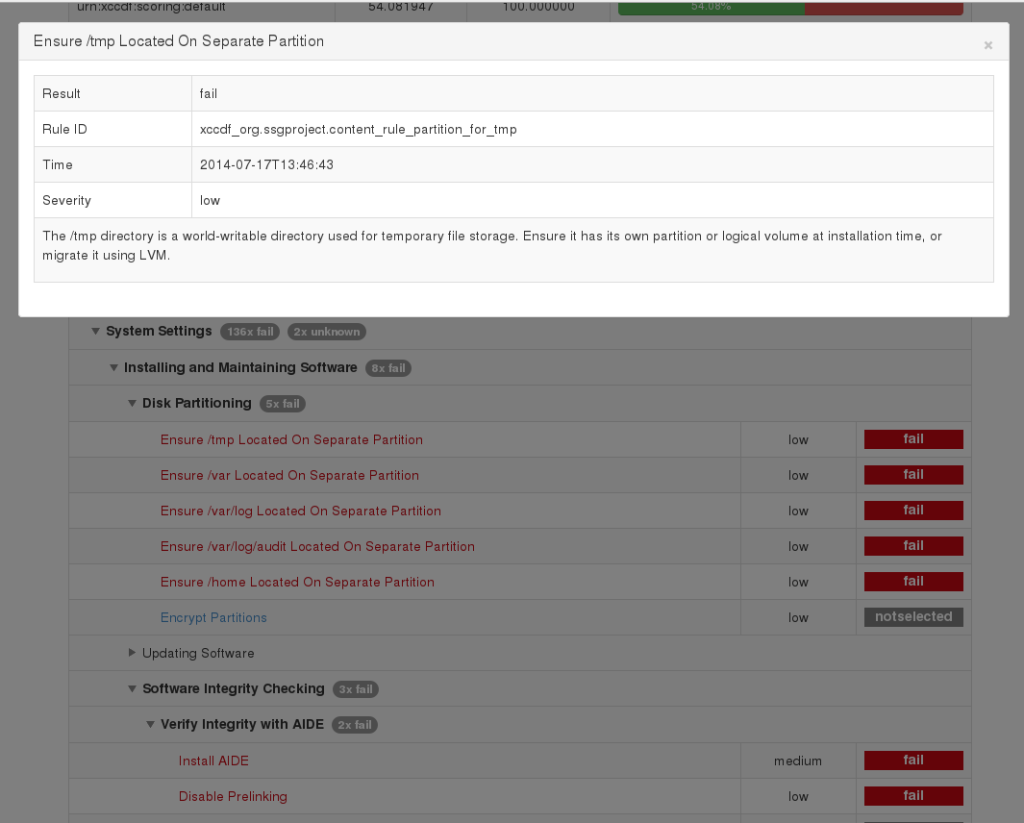
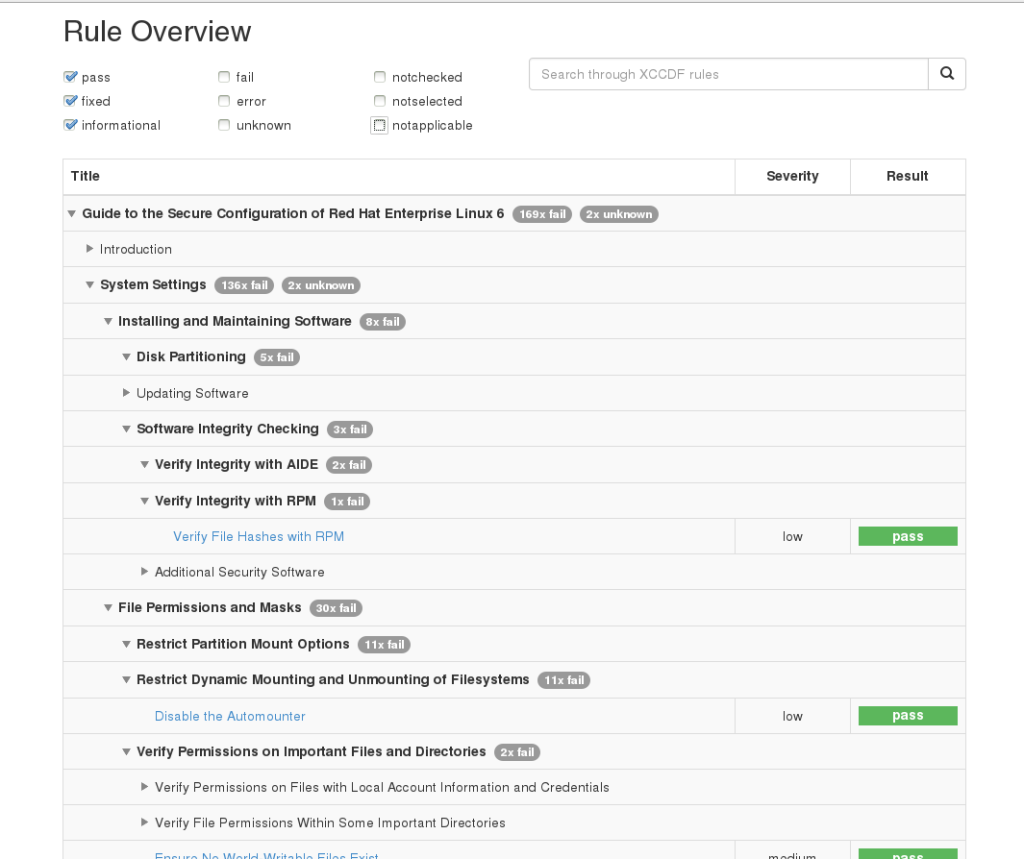
Generated sample
All the usual disclaimers apply. This is not the final version, a lot more than is necessary is bundled, not everything works.
Open the out.html file in a reasonably modern web browser.
openscap-xsl-prototype-part2.tar.gz
More feedback?
Would appreciate feedback again. I plan to continue working on this next week.
Perhaps, you could turn ‘notselected’ and ‘notapplicable’ off by default?
I find the notapplicable very, very useful…. at least for now.
Many legacy tools (e.g. SECSCAN) would report results saying (for example) /etc/httpd.conf has invalid permissions, even if httpd wasn’t installed. So SysAdmins would go install httpd just to pass this rule.
As users begin to transition from legacy tooling to OpenSCAP, it’d be great to show ‘notapplicable’ in the default output just so SysAdmins know they still passed that check
notselected is a no-brainer, that will be off by default. I think notapplicable should also be off by default, as it doesn’t apply to the machine. I will leave it on by default for now and we’ll see.