I would like to thank Brent Baude, Zbynek Moravec, Simon Lukasik, Dan Walsh and others who contributed to this feature!
Introduction
Containers are a very big topic today, almost all businesses are looking into deploying their future services using containers. At the same time, container technology is transitioning from being a developer toy tool to something that businesses rely on. That means that container users are now focusing on security and reliability.
In this blog post we will discuss a new security related feature in Project Atomic that allows users to check whether their containers have known vulnerabilities. This allows the users to catch and replace containers that have vulnerabilities and thus prevent exploits.
Motivation
Vulnerabilities are potentially a very costly problem for production deployments — internal or customer data leaks, fraud, … The bigger the deployment with more different containers images being used the tougher it gets to track vulnerabilities. Having a tool that can scan all containers we have deployed for vulnerabilities without affecting services would clearly help a lot.
Installation
We will need:
- Project Atomic 1.4 or higher
- openscap-daemon 0.1.0 or higher
- openscap 1.2.6 or higher
There are two major setups that we will discuss.
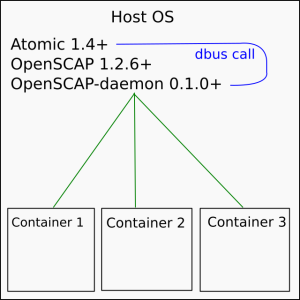
Everything on the same host (simple)
We could install all 3 parts on the host computer and then scan containers that are on that computer.
# assuming Fedora 23 dnf install atomic dnf install openscap-daemon systemctl enable openscap-daemon systemctl start openscap-daemon
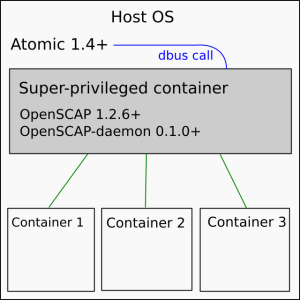
OpenSCAP in SPC (preferred)
We could install Atomic on the host computer, then install a super-privileged container with openscap-daemon, openscap and Atomic inside. The host Atomic will request the SPC to scan containers on the host machine.
This arrangement seems more tricky and complex but in the end is easier to manage because we can just pull the latest version of the SPC to install and/or update.
# assuming Fedora 23 and a self-built SPC dnf install atomic git clone https://github.com/OpenSCAP/openscap-daemon.git cd openscap-daemon/atomic docker build f23_spc # replace ID with the final ID that `docker build` gives you atomic install $ID atomic run $ID
# assuming Fedora 23 and a pre-built SPC # TODO
Usage
OK, now we have all the bits we need. Let’s use them.
# scanning a single container atomic scan $ID # scanning a single container image atomic scan $ID # scanning all images and all containers atomic scan --all
Example output:
$ atomic scan 82ad5fa11820 Scanning... Container/Image Cri Imp Med Low --------------- --- --- --- --- 82ad5fa11820 1 2 7 2
$ atomic scan --detail 82ad5fa11820 Scanning... 82ad5fa11820 OS : Red Hat Enterprise Linux Server release 7.1 (Maipo) Critical : 1 CVE : RHSA-2015:1981: nss, nss-util, and nspr security update (Critical) CVE URL : https://access.redhat.com/security/cve/CVE-2015-7181 RHSA ID : RHSA-2015:1981-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-1981.html Important : 2 CVE : RHSA-2015:2172: glibc security update (Important) CVE URL : https://access.redhat.com/security/cve/CVE-2015-5277 RHSA ID : RHSA-2015:2172-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2172.html CVE : RHSA-2015:1840: openldap security update (Important) CVE URL : https://access.redhat.com/security/cve/CVE-2015-6908 RHSA ID : RHSA-2015:1840-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-1840.html Moderate : 7 CVE : RHSA-2015:2199: glibc security, bug fix, and enhancement update (Moderate) CVE URL : https://access.redhat.com/security/cve/CVE-2013-7423 RHSA ID : RHSA-2015:2199-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2199.html CVE : RHSA-2015:2159: curl security, bug fix, and enhancement update (Moderate) CVE URL : https://access.redhat.com/security/cve/CVE-2014-3613 RHSA ID : RHSA-2015:2159-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2159.html CVE : RHSA-2015:2155: file security and bug fix update (Moderate) CVE URL : https://access.redhat.com/security/cve/CVE-2014-0207 RHSA ID : RHSA-2015:2155-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2155.html CVE : RHSA-2015:2154: krb5 security, bug fix, and enhancement update (Moderate) CVE URL : https://access.redhat.com/security/cve/CVE-2014-5355 RHSA ID : RHSA-2015:2154-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2154.html CVE : RHSA-2015:2131: openldap security, bug fix, and enhancement update (Moderate) CVE URL : https://access.redhat.com/security/cve/CVE-2015-3276 RHSA ID : RHSA-2015:2131-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2131.html CVE : RHSA-2015:2108: cpio security and bug fix update (Moderate) CVE URL : https://access.redhat.com/security/cve/CVE-2014-9112 RHSA ID : RHSA-2015:2108-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2108.html CVE : RHSA-2015:2101: python security, bug fix, and enhancement update (Moderate) CVE URL : https://access.redhat.com/security/cve/CVE-2013-1752 RHSA ID : RHSA-2015:2101-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2101.html Low : 2 CVE : RHSA-2015:2140: libssh2 security and bug fix update (Low) CVE URL : https://access.redhat.com/security/cve/CVE-2015-1782 RHSA ID : RHSA-2015:2140-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2140.html CVE : RHSA-2015:2111: grep security and bug fix update (Low) CVE URL : https://access.redhat.com/security/cve/CVE-2015-1345 RHSA ID : RHSA-2015:2111-00 RHSA URL : https://rhn.redhat.com/errata/RHSA-2015-2111.html
Future
We are working to get all of those parts packaged and then publish the ready-made SPC. In the future `atomic scan` may even pull it automatically so no installation other than Atomic should be required.
2 thoughts on “atomic scan and openscap-daemon”