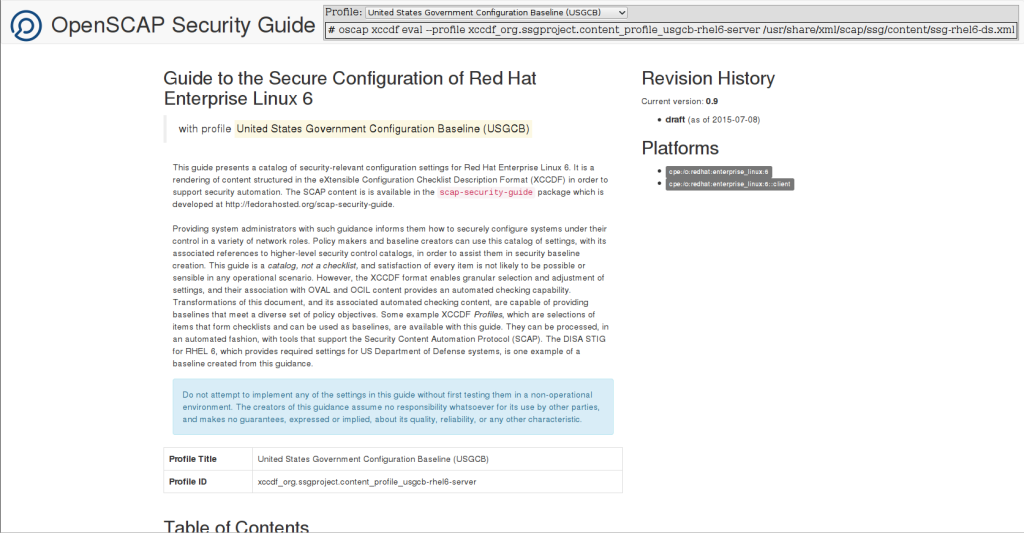
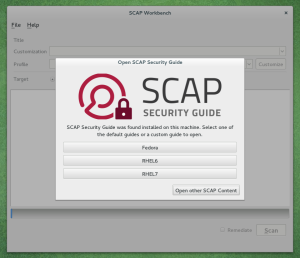
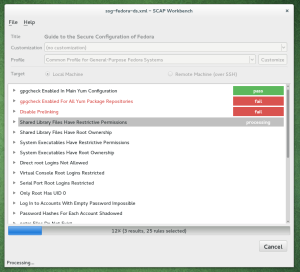
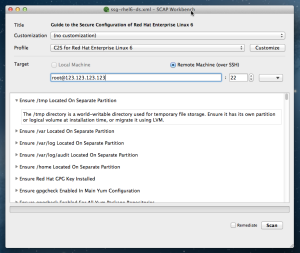
Recently I have been working on oscap-vm — a script that allows SCAP evaluation of virtual machines and virtual machine storage images. In a way it is similar to the other OpenSCAP wrapper utilities — oscap-ssh and oscap-docker. It was merged to OpenSCAP and will be part of 1.2.7 release, so let us introduce it.
oscap-vm mounts the storage of a VM and sets the oscap tool to scan it in offline mode. That means that you can scan a virtual machine from the host without installing OpenSCAP on it — you can perform an agent-less SCAP scan. Root rights are not required, if you are permitted to access and change the VM you are permitted to run oscap-vm on it. The virtual machine storage is mounted read-only, there is no risk of damage to the filesystem. Because of this you cannot automatically remediate a VM using this tool. If you want remediation functionality for virtual machines and containers, please tell us.
Both XCCDF and OVAL evaluation are supported. You can use plain XCCDF files, source datastreams or plain OVAL files.
Let’s go over a few use-cases. I am using a virtual machine called rhel7.2 in the following examples.
Evaluate a running VM
$ oscap-vm domain rhel7.2 xccdf eval --profile xccdf_org.ssgproject.content_profile_stig-rhel7-server-upstream /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xml Mounting guestfs domain 'rhel7.2' to '/tmp/tmp.c69yOdlBNZ'... Title Encrypt Partitions Rule xccdf_org.ssgproject.content_rule_encrypt_partitions Ident CCE-27128-8 Result notchecked [snip] Title Create Warning Banners for All FTP Users Rule xccdf_org.ssgproject.content_rule_ftp_present_banner Ident CCE-RHEL7-CCE-TBD Result pass Unmounting '/tmp/tmp.c69yOdlBNZ'...
Evaluate a storage image
$ oscap-vm image /var/lib/libvirt/images/rhel7.2.qcow2 xccdf eval --profile xccdf_org.ssgproject.content_profile_stig-rhel7-server-upstream /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xml Mounting guestfs image '/var/lib/libvirt/images/rhel7.2.qcow2' to '/tmp/tmp.PgfWcB0R4g'... Title Encrypt Partitions Rule xccdf_org.ssgproject.content_rule_encrypt_partitions Ident CCE-27128-8 Result notchecked [snip] Title Enable SSH Warning Banner Rule xccdf_org.ssgproject.content_rule_sshd_enable_warning_banner Ident CCE-27314-4 Result fail Title Create Warning Banners for All FTP Users Rule xccdf_org.ssgproject.content_rule_ftp_present_banner Ident CCE-RHEL7-CCE-TBD Result pass Unmounting '/tmp/tmp.PgfWcB0R4g'...
Check VM for CVE vulnerabilities
$ wget http://www.redhat.com/security/data/oval/Red_Hat_Enterprise_Linux_7.xml $ oscap-vm domain rhel7.2 oval eval Red_Hat_Enterprise_Linux_7.xml Mounting guestfs domain 'rhel7.2' to '/tmp/tmp.NbvfmaKHbZ'... Definition oval:com.redhat.rhsa:def:20151852: false Definition oval:com.redhat.rhsa:def:20151840: false Definition oval:com.redhat.rhsa:def:20151834: false Definition oval:com.redhat.rhsa:def:20151793: false [snip] Definition oval:com.redhat.rhsa:def:20140685: false Definition oval:com.redhat.rhsa:def:20140684: false Definition oval:com.redhat.rhsa:def:20140680: false Definition oval:com.redhat.rhsa:def:20140679: false Definition oval:com.redhat.rhsa:def:20140678: false Definition oval:com.redhat.rhsa:def:20140675: false Evaluation done. Unmounting '/tmp/tmp.NbvfmaKHbZ'...